Authenticators from Google and Microsoft are already well-established, but the newly released Proton Authenticator may be worth the switch. Proton is the company behind Proton Pass, our top password manager for those who prioritize privacy, as well as other services like Proton Mail and Proton VPN. While Proton Pass has an integrated two-factor authentication (2FA) feature on its premium tier, anyone can use Proton Authenticator at no cost, even if you rely on a different service for password management.
How Proton compares to other authenticator apps
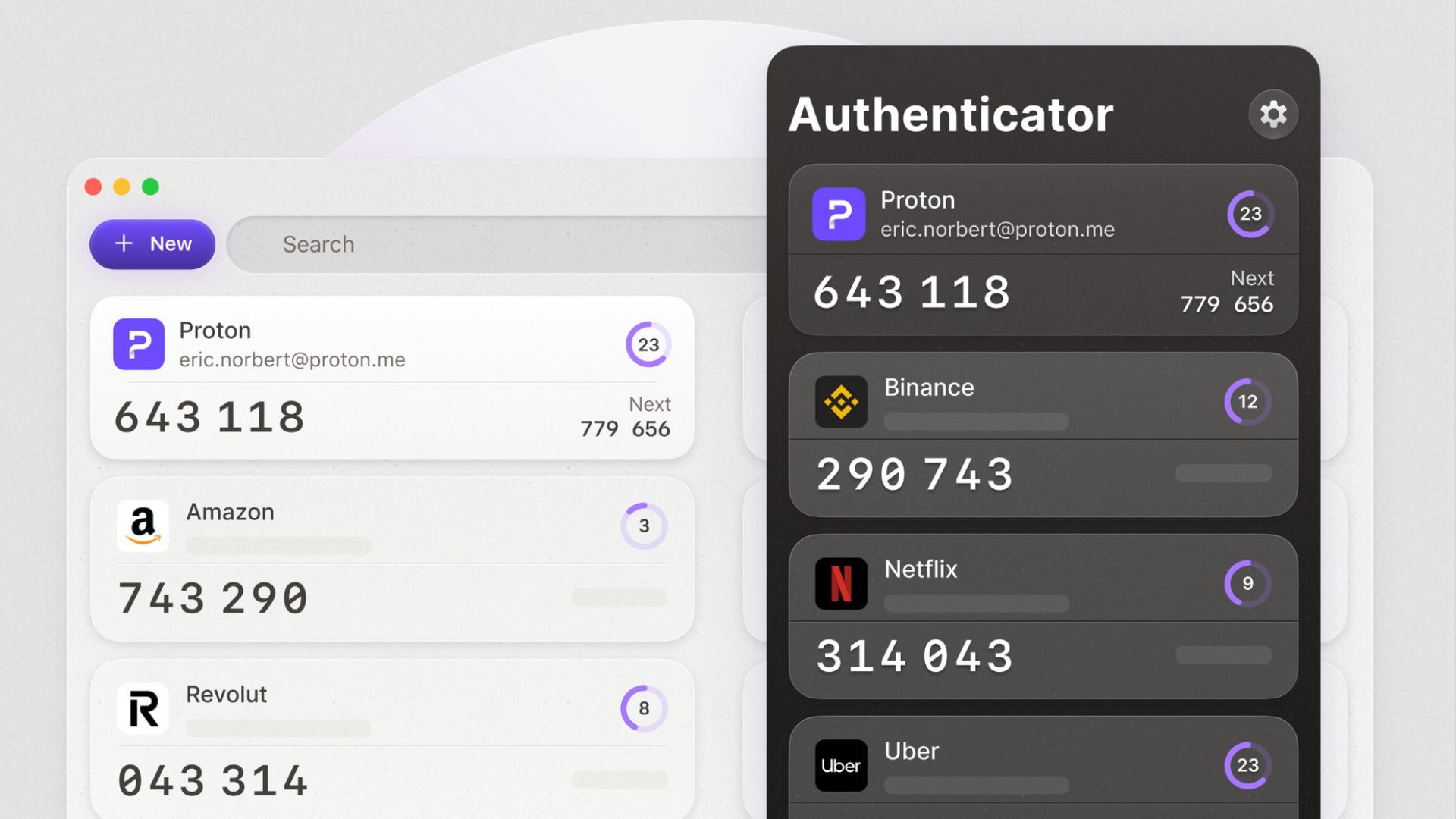
Functionally, Proton Authenticator isn’t that different than other popular apps like Google Authenticator and Microsoft Authenticator or alternatives like Duo and Authy. You can add time-based one-time passwords (TOTPs) manually or by scanning a QR code as well as import some or all of your existing codes from authenticator apps that offer this feature (Google does, Microsoft does not). In my testing, it was easy to screenshot and save the QR codes from Google Authenticator and upload them from my photos into Proton Authenticator, which quickly populated all of my codes.
For added security, Proton Authenticator can be locked behind biometrics like Face ID and hide your codes from view (which is helpful if you simply need to copy and paste on the same device). Codes refresh every 30 seconds, and Proton shows you both the current TOTP and the one that will populate next. While most authenticators are limited to iOS and Android, Proton also supports Windows, macOS, and Linux with encrypted syncing between devices.
Again, authenticator apps are largely similar in both form and function, but Proton Authenticator has a potential advantage in that it comes from a privacy-first company. Unlike most competitors, the platform is open source and doesn’t include any ads or tracking, so it’s well worth considering if you want to move away from services from Google and Microsoft. (Bitwarden, another excellent open-source password manager, also offers a free, standalone authenticator app.)
Given the regularity of data breaches and the ubiquity of phishing schemes that aim to compromise your data, you should have multi-factor authentication (MFA) enabled on any account that offers this extra layer of security. As I’ve written, some authentication methods—like SMS codes—are still easily compromised via phishing methods like adversary-in-the-middle attacks. Biometrics and hardware keys are some of the most secure alternatives, but an authenticator app is also preferable to SMS because TOTPs are generated locally on your device and change every 30 to 60 seconds rather than sent via unencrypted text.